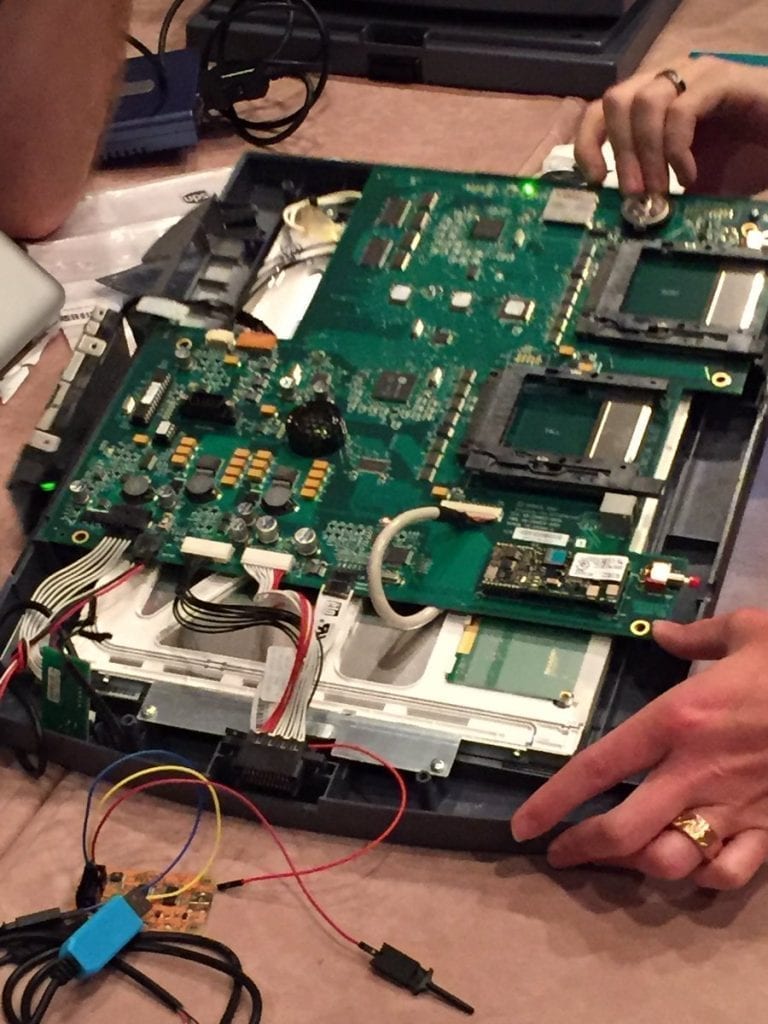
The world lives with some stark realities of the lack of democracy, the vote is the weapon of the people, but when the people vote it is disarmed. At DEF CON, at the famous hacker conference, it took 90 minutes to “hack” a voting machine used in the United States. The United States has always been a country where democracy has had “authoritarian relief”, even though the voting system is somewhat “strange” to ordinary people. Following the failure of the 2000 presidential election count, the US has invested heavily in electronic voting systems – but by all accounts, they have not invested so much in a security system for this voting system.
This year, at the DEF CON hacker conference held in Las Vegas, 30 computerized ballot boxes used in the US elections in the White House race were “hacked” first physically to gain access to the inside of them, for later Show what they had hidden inside.
— Bradley Barth (@BBB1216BBB) July 28, 2017 In less than 90 minutes, the first cracks in the system’s defenses began to appear, revealing a low level of embarrassing security. Next, a machine was hacked by Wi-Fi. “Undoubtedly, our voting systems are weak and susceptible. Thanks to the contributions of the hacking community today, we have discovered even more about how weak systems are”. Said Jake Braun, who sold the founder DEF CON Jeff Moss the idea earlier this year. “The scary thing is that we also know that our foreign adversaries – including Russia, North Korea, and Iran – have the ability to “hack” also in the process of undermining the principles of democracy and threaten our national security”. The Diebolds machines to Sequoia and Winvote equipment were purchased on eBay or at government auctions and an analysis by “hackers” at DEF CON, these voting machines revealed an unfortunate situation. Some were running very outdated and exploitable software – with uncorrected versions of OpenSSL, Windows XP, and CE. Some of these machines had open USB physical ports that could be used to install malicious software to adulterate votes. It’s one thing to physically have the box in front of us and try to do something on that machine. Of course, the officials who validate and follow the electoral process would detect and stop the attack. Another thing is in aerial form, by Wi-fi, from a distance, we can get access to the machine and manipulate it. Apparently, some of the boxes included poorly secured Wi-Fi connection. A WinVote system used in previous elections appears “hacked” via Wi-Fi and the MS03-026 vulnerability of WinXP enabled INFOSEC academic Carsten Schurmann to access the machine from his laptop via RDP. Another system can potentially be attacked remotely via OpenSSL by taking advantage of bug CVE-2011-4109.
— Robert McMillan (@bobmcmillan) July 28, 2017
Better safe than SORRY
Those responsible for this “security test” said the WinVote machine was not fully secure and that the intrusion would have been detected and logged, so there is no reason to panic. And not all the attacked equipment is used in the current elections, there are several models already discontinued.
— Victor Gevers (@0xDUDE) July 28, 2017 However, these attacks show that there may be remote access to equipment and that local election officials are not at all prepared to detect this remote intrusion, especially now with US-Russian relations in an unfriendly state. Those responsible for this test want the results to be seen as a wake-up call. So, what do you think about this vulnerability? Simply share your views and thoughts in the comment section below.
Δ